I was sure I saw a link to this from Daringfireball, but can’t seem to find it again. Anyway. I’ve been running Lockdown on my phone for a couple of weeks now, and it’s been working great. It’s an app that integrates with the VPN feature in iOS, so all network requests get pushed through the app for filtering. It doesn’t actually do a VPN, but uses that as a hook to block domains that are requested in any app. There are app-specific tools like Firefox Focus, or Safari-tools like Better Blocker. But Lockdown should work in for any app because it runs at the VPN network level (so it could do things like blocking embedded marketing trackers that report when you’ve viewed an email in Mail, etc…).
It’s open source and free (for now?), but I haven’t gone through the code on GitHub (or, for that matter, have any way to verify that the code on GitHub is the code that’s compiled into the app). For all I know, it could be doing some nefarious stuff with my network requests. There’s no way to really tell. But it claims to work, and it blocks all kinds of privacy-invading adware, and other network-ne’er-do-wellers.
Lockdown’s privacy policy looks pretty clear, and states that nothing leaves the phone and all filtering happens locally. I’d feel a bit more comfortable if there was a third-party audit of the app, to know if it’s doing what it claims to be doing (and only what it claims to be doing). Handing an app VPN-level access to my phone is a rather big act of faith…
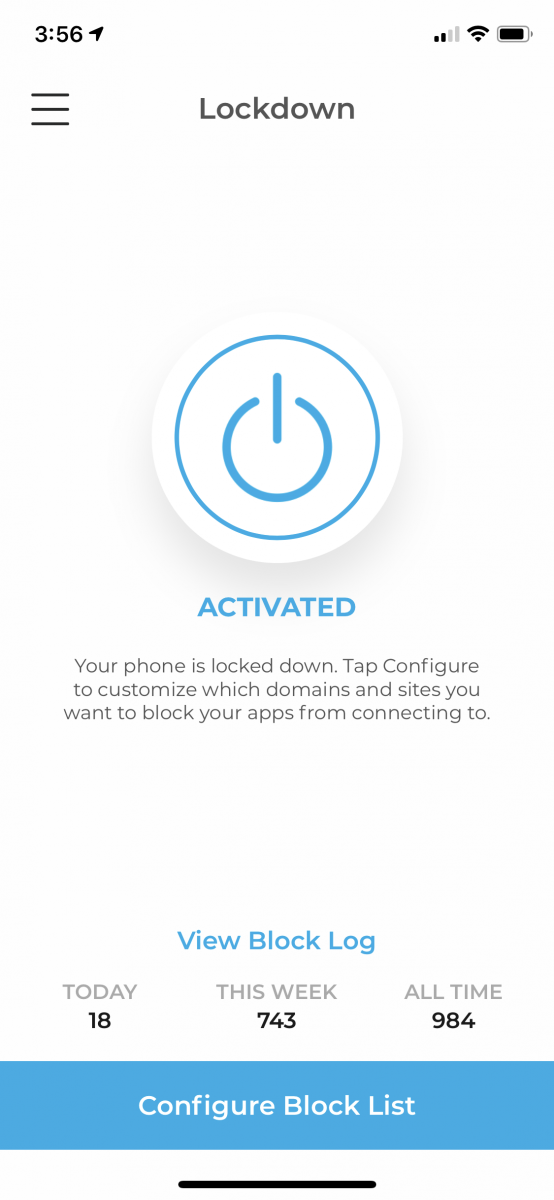 That’s all there is. Turn it on. Let it run. Assume it’s not being evil…
That’s all there is. Turn it on. Let it run. Assume it’s not being evil…
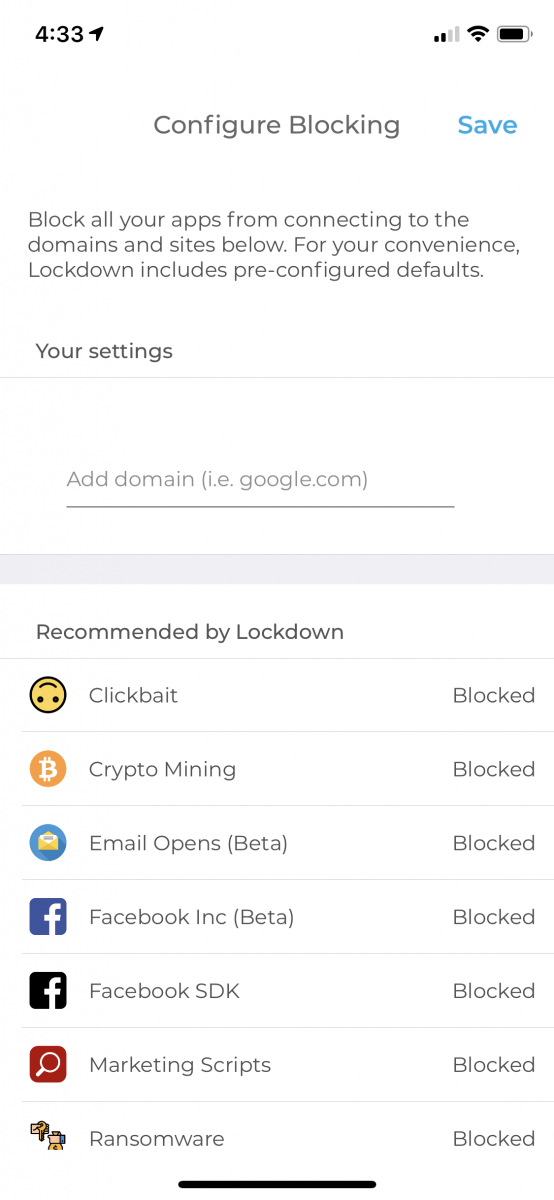 Pick the stuff you want to block and/or add your own filters…
Pick the stuff you want to block and/or add your own filters…
 It tracks the stuff it claims to have blocked. This is what came up after loading a few websites in Safari.
It tracks the stuff it claims to have blocked. This is what came up after loading a few websites in Safari.
I’ll try running it for awhile longer - it seems to do a great job in stamping out the domains that are associated with internet crapware and privacy invasion. It feels a bit like the shared killfile in William Gibson’s Idoru…